MANAGED SECURITY SERVICE PROVIDER (MSSP)
As your managed security service provider mssps specialists, we take security issues out of your hands and handle them with the experience and knowledge that comes from years of safeguarding companies just like yours. We specialize in highly regulated environments utilizing controls such as HIPAA, GDPR, CIS, and NIST.
With managed security services, your staff will be trained and empowered, while your technology is kept airtight, leaving the administration, planning, and processing to the experts—us.
Malicious Connection Attempts Blocked Each Day
Malicious Connection Attempts Blocked Each Day
Network Flow Records Inspected Per Day
Network Flow Records Inspected Per Day
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Downloaded Malware Caught & Eliminated with Zero Incidents Last Year
Workflow Events Logged Everyday
Workflow Events Logged Everyday
A strong network security program requires a deep understanding of the threats facing your business, as well as the skills and tools necessary to combat those threats.
Our AI-gathered cybersecurity services intelligence, threat prevention and analysis helps us to identify and stop security threats before they happen. Our security team has the most up-to-date information on new malware, phishing techniques, ransomware, and attack vectors that hackers are using to steal data. These insights are translated into vigilant cybersecurity defenses for our clients.

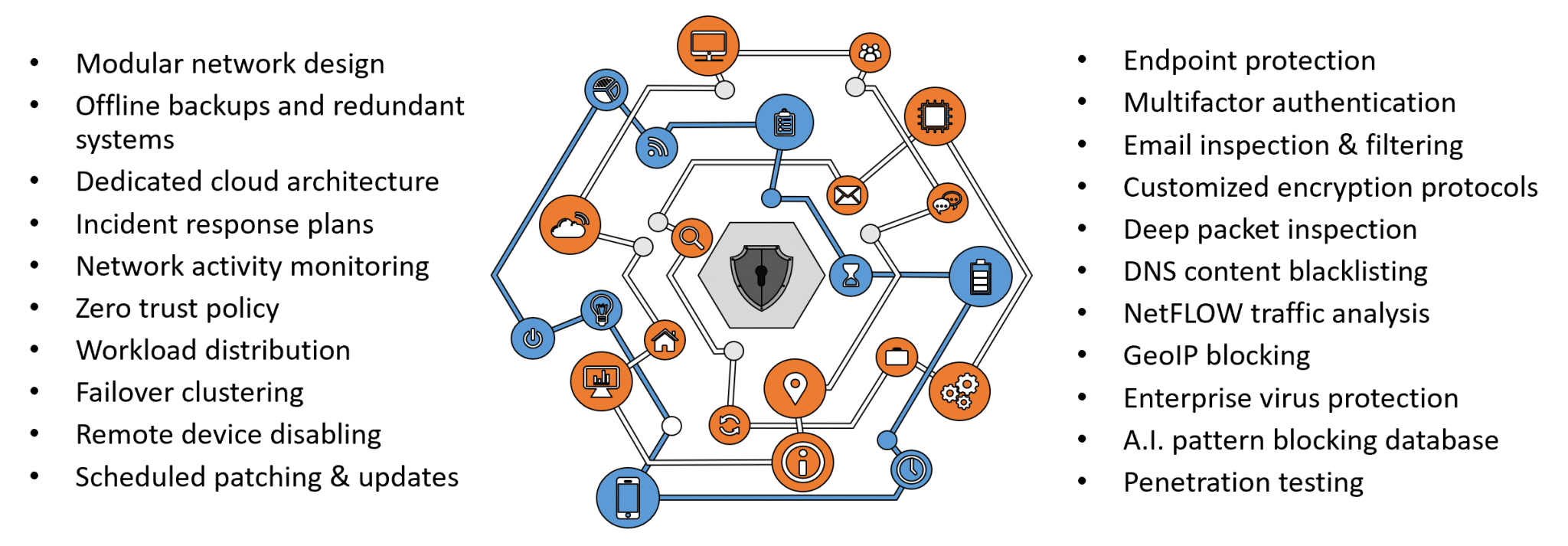
Vulnerabilities are addressed through a multi-tiered approach with solutions like vulnerability scanning that encompass your entire network infrastructure. There’s no such thing as a one-size-fits-all cybersecurity or network security. Each company is uniquely vulnerable, so every solution is thoughtfuly currated and customized, starting with a thorough risk & vulnerability assessment.
We prioritize layered cybersecurity protection, beginning with a sturdy network perimeter composed of a firewall, a network management system, and regular network inspections. We then include proactive monitoring of your systems, including anti-virus and anti-malware software, DNS filtering, and anti-spam protection. Most importantly, we recommend investing in cyber training for your staff—your employees are the first and finest line of cyber defense.
A Managed Security Services Provider for New York, New Jersey, & Connecticut Businesses
Information Security Management That Proactively Protect Against Today’s Complex Security Threats
Get a Free Cybersecurity Audit
Understand your security threat exposure with a free cybersecurity risk assessment. Great actionable steps you can take to gain a strategic upper hand. We offer risk assessment services specifically designed for companies operating under HIPAA, PCI DSS, Sarbanes Oxley, or DFARs regulations.
When you put Protected Harbor in charge of your information security, we go on the offensive with an arsenal of industry-leading tools backed up by a security operations team who knows their stuff. Our dedicated threat hunters make it their mission to gain a firm grip over the ever-changing arena of information security and stop threats before they start. When you join The Protected, you’ll finally experience security and peace of mind.
Protected Harbor’s Security Operations Center team is staffed with certified cloud computing, security techs, and threat hunters from around the globe, operating 24/7/365 as an optional part of your cybersecurity defenses. We are continuously monitoring, detecting, and remediating threats to keep your data protected as part of our elite service plans.


Protected Harbor continuously collects flow data to aggregate, analyze, and visualize network details for real-time viewing or historical archiving.
Our threat protection dashboard gives our proactive monitoring team a view of possible threats contacting or attempting to contact the network, including public threats based on IP reputation, high-risk internal clients based on flow count, visual hot spots of inbound connections, top block ports, and recently blocked traffic.
Who’s doing the most traffic? Are we being flooded? What types of traffic are using the most bandwidth? These questions and more are answered by filtering for results on the Top Talkers Dashboard. We can even drill down further onto flow details to find specific traffic streams to analyze from an individual protocol or address.
With Protected Harbor compromised credentials, unmitigated vulnerabilities, and network intruders are no longer a threat to critical data. We use AI to build a database of bad actors and a variety of monitoring and blocking methods to provide protection for internal networks at various common attack vectors.



